
CERT-In postpones rollout of VPN guidelines: The government postponed the rollout of its new privacy rules for VPN providers, data centres and cloud service providers for another three months. The guidelines under sub-section (6) of Section 70B of Information Technology Act, 2000 cover information security practices, procedures, prevention, response, and reporting of cybercrimes.
The new rules issued by the Indian Computer Emergency Response Team (CERT-In) was postponed following a request for extending the time limit by MSMEs. The extension will help companies build technical infrastructure to comply with the rules. The service providers are also granted more time for implementation of mechanisms relating to the validation of details given by subscribers and customers.
Under the new guidelines, VPN service providers are expected to store user data for five years even after the client has stopped availing the services. The government wants service providers to share user data whenever it is required for legal investigations. The service providers are required to store the following information:
- Validated name of people using the services.
- Specific time period of using the services. IP address allotted or used by the user during the course of service.
- Email address, IP address and time stamp used at the time of registration.
- The purpose of hiring the services.
- Validated address and contact number.
- Ownership pattern of client hiring the service.
The new rules mandate data centres, virtual private servers (VPS), and cloud services to collect and store data. There are several serious concerns about these directions. Data governance experts and VPN companies have raised concerns over the potential threat to data privacy under this policy. This has led to intense discussion among internet and cyber communities. Companies, policy experts, lawyers and other stakeholders are deliberating on the new policy’s financial and legal feasibility.
READ I Climate change: From Paris to Sydney, extreme weather events send out dire warning
Compliance burden on service providers
It is onerous for the service providers as the compliance cost will increase due to emphasis on data localisation. It is still unclear if there is a need for companies to build additional infrastructure, or if they are allowed to outsource to third-party data storage companies. Insights on the accuracy of data provided by the users are still lacking. To get relevant information from users, companies may have to deploy additional technology – leading to higher costs. Further, the directives require the service provider to designate a point of contact (POC) to mediate with CERT-In. There is no clarity on whether the POC should be from India or can be a foreign national.
The order issued by CERT-In also directs companies to report any data breach within six hours of noticing them and main ICT logs for six months. To do so, companies might have to install technologies like End-point Detection and Response leading to an increase in maintenance cost. Not complying with this directive could be punishable with prison sentence. Newly issued orders hinder ease of doing business, and foreign companies may rethink their decision to operate in India. Some VPN companies providing services in India such as Express, Nord, Surfshark, and Proton are evaluating their future in the country.
The government’s concerns are genuine, but it comes at the cost of citizens’ privacy at large. Nord VPN service providers says while it respects the government’s intention to strengthen cybersecurity, more intense discussions with stakeholders over new rules are expected. The Information Technology Industry Council also expressed concerns over the six-hour time frame for reporting cybersecurity breaches.
The players have requested the government to align the rule with the global practice of giving 72 hours for enterprises to contextualise and investigate such incidents. Almost all service providers want to follow a no-log policy where they will not store any user data as it is against their company policies and technical feasibility.
READ I India’s coal riddle: Surging imports despite huge reserves
India is seeking global action against the use of technologies including VPNs, end-to-end encrypted messaging services, and blockchain-based technology by terrorists. In suggestion to members of an ad hoc committee of the United Nations, India said anonymity, scale, speed, and scope offer the possibility of being untraceable for a terrorist to conduct anti-national activities, which is a serious threat to the world.
India plans to expand its clampdown on VPNs by banning government employees from using VPNs and cloud services. The National Informatics Center (NIC) issued guidelines to sensitise employees from a cyber security perspective. It asked employees not to store any confidential data on non-government cloud services like google drive and dropbox. It also urged employees to avoid using CamScanner, a Chinese application that was banned in 2020 over cyber security concerns, to scan official government documents.
Individuals or companies use VPNs to encrypt their data over the internet and protect themselves with anonymity. However, under the new rules, VPN users in India will not enjoy any kind of anonymity, and even after any citizen stops using VPN service, their data will not be erased. VPNs create a secure and private connection between a user and server.
The rules also violate the right to be forgotten. However, these directives are not mandating corporations to use VPNs. The fundamental nature of VPNs is not to hold or collect user data and provide them with anonymity. A VPN works by undocking the web addresses individual visits from their IP address, so ultimately the demand from the government to collect consumer data is against the technical nature of a VPN. Large service providers like Nord, Surfshark, and Express are all RAM-only servers where data stored inside them is wiped clean every time they get restarted.
“The virtual asset service providers, virtual asset exchange providers and custodian wallet providers (as defined by the ministry of finance from time to time) shall mandatorily maintain all information obtained as part of Know Your Customer (KYC) and records of financial transactions for a period of five years so as to ensure cyber security in the area of payments and financial markets for citizens while protecting their data, fundamental rights and economic freedom in view of the growth of virtual assets,” clause (vi) read.
Regulating VPN services up to such a high level can affect whistleblowers, journalists and activists. When requirements of data localisation are combined with data retention directives, it raises serious concerns about mass surveillance. The government has the intention of enhancing cyber security, however, implementing such a policy in the absence of a data protection law could actually act the other way around. Data privacy for all is the prerequisite of strong cybersecurity.
Companies storing user data for five years and sharing it with the government on legal request can lead to data breaches or malicious attacks which can make an individual’s privacy vulnerable. As per the estimates of Surfshark VPN, India is ranked third among countries with the most data breaches with around 8.7 crore users affected.
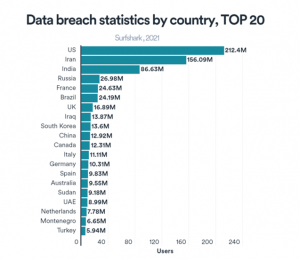
India is among the top 20 VPN users in the world. The country recorded more than 270 million VPN users in 2021 ie. around 20% of the population. As per the Global VPN usage report 2020, India was the second-largest market for VPNs where 45% of the internet usage happened through VPN.
VPN guidelines: The way forward
The Supreme court has considered the Right to Privacy as the fundamental right under Article 21 in the Aadhar data breach case, 2017. The Union government drafted the Personal Data Protection Bill in 2019, which has been updated as the Data Protection Bill 2021. The CERT-In orders are violative of the provisions of the Data Protection Bill which is yet to become a law. As per section 18(1)(d) of the Data Protection Bill, data principals (users) have the right to erase their personal data that no longer serves the purpose for which it was collected. The bill restricts retention of personal data after its purpose is fulfilled.
India witnessed a total of 11,58,208 cyber security incidents in 2020-21. Such attacks increased to 12,13,784 by October2021. Among these, about 87,050 were against government organisations. As cryptos have taken huge clamour, the government’s concern over its usage is valid to avoid fraud and illegal conduct in the crypto market. while the government also needs to define its data governance strategy in the Web 3.0 ecosystem.
The government must re-define its position on directions issued by CERT-In:
- The approach of collecting logs for five years is extraordinary where the timeframe is a huge concern,
- Cybercriminals use VPNs to conduct illegal acts on internet including hacking systems, and engaging in illegal activities on the dark net, due to which the government wanted user data to be stored. However, the government should ensure data holding and processing to only analyse the threats to national security and cybersecurity. Here, the state needs to establish a process that can rationalise the granting of exemptions to the government, and this procedure of granting exemptions should be made public over a period of time.
- Seeking deliberate multi-stakeholder consultancy in order to draw a balance between right to privacy, cybersecurity/ national security, and ease of doing business.
- The current definition of a reportable incident is too vague to include activities like probing and scanning which are everyday activities. It is not useful for companies and Cert-In to spend time and resources in gathering, transmitting, receiving, and storing such a large volume of insignificant data.
- Securing logs and maintaining them for the Indian government is not a good practice. Such repositories of logged data can be a target of global cyber threats.
- The new guidelines are not aligned with certain provisions of the Data Protection Bill, which is going to be the first and unique data protection law for India.
(Shiv Chhatrala is a master’s student at Christ University, Bangalore.)
